Ariane 5, Boeing’s 787 Dreamliner and a 105-year old swedish lady who has to go to preschool. All these events have one thing in common – they were caused by software errors. Today we show you how the number 2,147,483,647 (two billion one hundred and forty-seven million four hundred and eighty-three thousand six hundred and forty-seven) connects to these historic incidents.
How Overflows Come to be
Basically a software solution works with variables. These variables include different types such as characters and numbers. Of course, we all have heard at some point that a computer works with zeros and ones, which are called bits. If a variable gets defined it is usually limited to a certain number of bits.
Let us assume that we define a variable which contains a natural number with 4 bits. Now we can represent numbers from 0 up to 15:

So, what happens if we want to perform an addition that can no longer be represented with 4 bits? For example, if we calculate 12 + 7 with 4 bit variables:
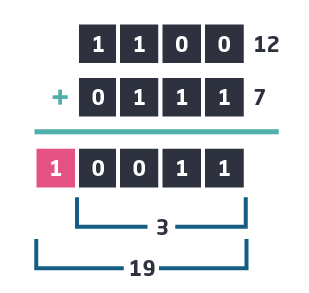
The surprising result is 3 and not 19, since 19 can not be represented by a 4 bit variable. To express the correct result we would need an extra bit, i.e. 5 instead of 4 bits.
This problem is called an “overflow”, which occurs when you try to store a number in a variable that does not fit into its range Hence, the number is larger than the maximum number which can be represented by that variable. Typically, this situation appears while performing arithmetic operations.
Furthermore, it should be mentioned that many software applications are using 32 bit variables that allow them to represent numbers in the range from -2,147,483,648 to +2,147,483,647. Developers often assume that roughly 2 billion positive numbers are quite sufficient and ignore the fact that an overflow can occur over time. In this case, just like in our demonstrative example, an overflow exists. If its data type is an integer, it is called an “integer overflow”. Overflows are oftentimes the cause for security breaches. The following examples demonstrate which unexpected and devastating consequences different kinds of overflows can provoke.
Only a few overflows made it into the history books. We have picked the most blatant three for you:
The epitome of a software bug of this kind is probably best demonstrated by the Ariane 5 rocket launch. On 4 June 1996, the unmanned rocket of the European Space Agency (ESA) was set off into orbit. On board were four highly complex satellites which should be brought into the sphere. However, after only 39 seconds the flight ended in a disaster: the rocket disintegrated into a ball of fire and smoke. Investigations have shown that the crash was not a mechanical failure. The main cause was a software bug that could have been easily detected by static analyses and unit tests.
The Ariane 5 was equipped by ESA with the identical software of the previous rocket model, the Ariane 4. The new space launcher reached a much higher velocity than the previous model. The system initiated a self-destruct sequence on exceeding a certain limit. Strictly speaking, the sideways speed was exceeded in this case. The resulting damage amounted to $ 500 million.
Another famous example of how a trivial “integer overflow” not only threatens the existence of a company but also put people’s life at risk is demonstrated by Boeing’s 787 Dreamliner. A bug crept into the plane’s software, which caused the control unit to switch to a fail-safe mode after 248 days of continuous operation. If this error occurs during a flight, the pilot loses control of the aircraft and a crash is the inevitable consequence. However, if you look at the figure more closely, 248 days in hundredths of a second are exactly 2,147,483,647. To solve this significant problem, Boeing had 2 solutions: Either restarting the control unit before the 248 days expired or, the much safer option, adequate software testing.
Probably the most famous overflow bug in history is the publicly hyped Millennium Bug, Y2K. The problem of the 2000s caused headaches for lots of developers: not all applications were designed to store years after 1999. Myriads of companies had to update their software solutions to avoid possible outages. However, at the turn of the new millennium serious consequences did not occur thanks to countless hours of hardworking programmers.
Although, twelve years later an amusing incident did happen: a 105 year old Swedish lady received an invitation to start preschool. Invitations were sent throughout the Swedish kingdom to children who had the final digits “07” in their year of birth. Developers did not consider that there were individuals born in 1907.
Automatic overflow detection
Overflows are one of the most common weaknesses of software applications. During the development of software, usually special attention is paid to avoid such problems. However, such care is neither efficient nor successful, as our selected examples demonstrate. This is true even for software projects in industries with high quality requirements.
Even simple programs often consist of several 100,000 lines of code. It is almost impossible to find every single problem in any program, let alone test such programs. The higher the complexity of an application, the more susceptible it is to software bugs. For exactly these reasons we have developed Symflower. Symflower generates unit tests fully automatically and finds potential overflows in every source code. Regardless of the number of lines of code and the complexity of the application. Even without any human influence.
More about the ease of unit testing can be found on our feature pages. Send us a request for a product demo and take a look at the future of software testing.